Symantec Enterprise Division: Sharing Ain’t Always Caring
Phishing and the Era of Abusing File Sharing Services
The holiday season is up. You’re all geared up for it. You’re about to log off from the workstation but you receive an email from one of the vendors with a subject of: Pending Invoice. You open the email which mentions that a payment is due and urgent payment is required. That’s all that’s written in the email. But to your surprise, the message asks you to click a URL to get insights on the invoice and the due payment. Hmm… The URL provided in the email is of course legit as it’s an online file sharing service URL. Everything seems to be working fine. You click on the URL, which routes to a legit online file sharing services portal and voila, there’s your file. Probably a .pdf extension file named as “invoice_for_payment.pdf”. All that’s remaining is to download the file, view the invoice and pay accordingly. But as soon as you open this file, instead of seeing an invoice, there is an instruction to click on a URL provided in this file to view the invoice. Once again you click on this new URL and then you are redirected to a pretty perfect legit login page. For authentication purposes, the page prompts for credentials. You look at your watch and enter the credentials in a hurry. Boom! You’re redirected either to an inactive webpage or if you’re lucky, to a proper legitimate webpage with fancy padlocks on the side of the URL.
What just happened?
For starters, you’ve been PHISHED! In 2019, Symantec observed a rise in the overall volume of phishing attacks abusing online file sharing services such as WeTransfer or hosted SharePoint. Phishers and other attackers have taken advantage of the increased popularity of these services. Surprisingly, one cannot think that only popular brands such as Box, WeTransfer, OneDrive are getting abused. Threat actors have also explored lesser known brands or new brands to target.
Host – Share – Phished!
A threat actor registers for a free account (using fake or stolen credentials) at some of the many online file sharing services. More sophisticated attackers research their target in more detail; if their target uses SharePoint, then so will they, as this improves the chances of stealing user credentials. Attackers then upload files containing links to phishing sites. All that is left is for the attacker to send messages to their targets, carefully composing the messages to make sure the recipients first open the messages, and then click on the links inside. Sometimes, an attacker’s job is made even easier by file-sharing services providing an option to share an uploaded file by email. The message sent by the file sharing provider might have a positive or neutral reputation and could therefore be less likely to be stopped by traditional anti-spam software. Below is sneak peak of phishing trends observed in 2019.
Top notch abused online file sharing services:
In 2019, Symantec’s telemetry and threat intelligence have reflected some of the popular file types and online file sharing brands been abused.
Statistical data clearly indicates that .pdf (69%) and .html (11%) are the favorite file types of threat actors used for hosting phishing content on online file sharing services portal. The telemetry also provides an insight on the top 2 most abused brands of online file sharing services: Box (17%); WeTransfer (11%). However, the abuse is not limited to these popular file sharing brands. Lesser known or new online file sharing services are also getting abused with this type of attack. Some of these include brands like HighTail, Filemail, Jottacloud, Livedrive, DocSend.
Anatomy of the phish attack:
As always, the not so secret ingredients to the success of this attack are sense of urgency and trust. Threat actors heavily rely on these two factors. In general, these emails masquerade as invoice or payment notifications messages with an overwhelming tone of urgency and limited or short body content. Such language is purposely injected in the email body so that when read, creates panic in the victim’s mind to perform the actions provided in the email. Threat actors tend to be good at reading minds. To add a cherry on the cake, threat actors use URLs of online file sharing services on which the phishing file is hosted. The potential victim hovers the cursor over the URL, looks at the https protocol at the start of the URL and therefore clicks on it. Here, the trust factor is gained by the threat actor. To reassure, the potential victim checks the webpage on which the URL in the email body has routed. This is a legit online file sharing services portal with a file awaiting to be downloaded. The email user is prompted to download the file to get an insight on the pending invoice. As soon as the file is downloaded and opened, it displays another URL which instructs the email user to click and provide authentication. This URL is the phish URL embedded within the file. The following series of screenshots depict the working of this attack. These images contain screenshots of actual phishing emails along with the preview of landing webpages:
Case 1: Phish attack abusing OneDrive services:
Email:

OneDrive webpage with .pdf file to download:

Case 2: Phish attack abusing WeTransfer services:
Email:

WeTransfer webpage with .htm file to download:

Case 3: Phish attack abusing Box services:
Email:

Box webpage with .pdf file to download:

The above screenshots follow the same pattern. These phish emails have key things to note:
- Use of legitimate online file sharing services to distribute phishing URLs. In other words, these services are used as platforms to deploy phishing kits or steal credentials.
- Email template contains batch of legit words or keywords in the content part.
- Phishing URLs are embedded within different file formats / types.
The above list makes it difficult for the traditional anti-spam filters / scanners to block such emails.
Detection against file sharing phishing messages:
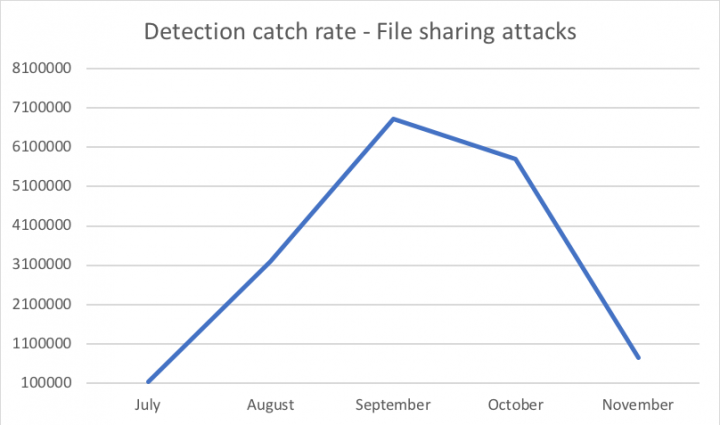
Predictive filtering system focused on URL and other email features are deployed in timely intervals to catch changes in the rapidly changing email threat landscape. With the help of predictive filtering system, threats that use email as a medium are filtered or blocked before they cause menace. This approach has also proved beneficial to detect the variation in these types of attacks and filter them down in terms of volume or scale. The below graph demonstrates the impact of detections added against file sharing services attacks. Based on 6 months (June - November) statistical data, the surge is observed during August – October 2019. This indicates that threat actors have not only abused popular online file sharing services but have also exploited lesser known services during this period. The detection catch rate has almost reached at a significant scale during this period. This is the same period that Symantec Enterprise Division (SED) joined Broadcom Corp. and teams at Symantec not only maintained focus to provide detection but also strived for comprehensive coverage against email threats.
Mitigation steps:
- Email users are requested to thoroughly check emails and if deemed suspicious, please report it to Symantec.
- Question any emails requesting actions that seem unusual or aren't following normal procedures.
- Analyze potential threats using analytics technologies that can pick up on the subtle differences between clean and infected emails and identify indicators of compromise.
- Conduct end-user awareness training to raise overall awareness of phishing among employees.
Defense mechanisms:
At Symantec, response teams strive hard to protect our valuable customers by introducing new defense mechanisms against such challenging attacks. An array of defense mechanisms is deployed in different layers at .cloud and Symantec Mail gateway level to block similar attacks.
- Symantec Email Security Cloud Data Protection: provides granular control to identify suspicious messages based on various indicators and helps to flag messages that are coming from outside the organization.
- Symantec Data Loss Prevention: helps combat the data theft scenario by seamlessly integrating with our Email Security solutions.
- Email threat isolation (ETI) from Symantec: checks emails and attachments for phishing URLs or malicious content hosted on them. This technology de-risks the threat scenario by providing an extra layer of protection that allows users to safely browse unknown or shady websites, without risk of malware infection or credential theft. Symantec Email Threat Isolation is offered both within the Symantec Email Security. cloud solution and also as a standalone product that works with other vendor’s email security solution.
Additionally, Symantec has made it a point to report abuse of online file sharing services URLs to their respective anti-abuse teams in a timely manner.









We encourage you to share your thoughts on your favorite social platform.