|
This is the third article in a four-part series that will examine privacy concerns as they relate to security. The first installment in the series examined hardware-based privacy issues and solutions. The second installment discussed software-based issues and solutions. This installment will discuss privacy issues that are particularly relevant to e-mail.
According to research conducted by Neilson NetRatings, e-mail is by far the most widely used application on the Internet. Unfortunately, e-mail should also be of great concern to people concerned about privacy. This article will help you assess the dangers that e-mail provide and give you ideas about how to safeguard your privacy while using it.
Securing Your E-Mail Client Program
If you asked most people what program they use the most each day, it's probably their e-mail client. For most Windows users, this means Outlook or Outlook Express (OE). This is problematic, of course, since out of the box both programs are dreadfully insecure. Fortunately, there are things that users can do to protect their privacy when using Microsoft's e-mail clients. Please note that I'm only going to cover aspects of these programs that directly pertain to privacy; going over the security aspects of Outlook and OE would require an article by itself.
Web Bugs in E-Mail
The biggest privacy danger to e-mail users is that of Web bugs, which I discussed at length in the previous article. Basically, a Web bug is a tiny invisible GIF image that a spammer or marketer (often the same thing) places into an HTML-formatted e-mail. With the Web bug, the spammer can tell when the recipient of the e-mail opens it because his server will track a hit when the Web bug is viewed, this lets him know that he has a live address. In addition, the spammer can also track if the recipient forwards the e-mail and when the new recipient opens the e-mail as well, thus gauging the effectiveness of the spam. Finally, the IP address of all readers of the e-mail can be transmitted to the spammer, which helps him link an e-mail address to a specific machine on the Internet.
The Preview Pane
There are several steps that e-mail users can take to block Web bugs; as an added bonus, some of these steps will help curb (but not prevent) the spread of viruses, something Outlook and OE make far too easy. First of all, turn off the Preview Pane function in Outlook. If the Preview Pane is on, a Web bug may be activated as soon as you select the e-mail from the list of messages in your inbox. To turn the Preview Pane off in Outlook, go to the View menu and uncheck "Preview Pane":
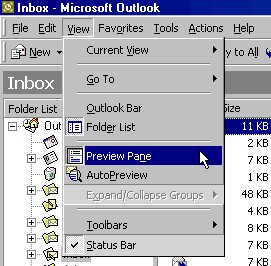
Fig. 1: Turn off the Preview Pane in Outlook
Do the same thing if you're using Evolution , the great e-mail program for Linux. If you're using Outlook Express, choose the View menu, then select "Layout ..." in order to open the Window Layout Properties dialog box. Uncheck the box next to "Show preview pane".

Fig. 2: Turn off the Preview Pane in Outlook Express
Finally, if you're using either the Mozilla or the Netscape e-mail program, choose the View menu, go to "Show/Hide", and then disable "Message Pane", as is illustrated below:

Fig. 3: Turn off the Preview Pane in Mozilla or Netscape mail
It's really easy to turn off the Preview Pane in your e-mail programs, and it will go a long way to protecting your privacy.
Disable JavaScript Support
To further protect yourself against e-mail spying, disable JavaScript. It's bad enough that e-mail clients support HTML, but there is absolutely no reason why they should also run JavaScript embedded in e-mail messages. (For a more detailed account of why HTML and JavaScript create insecurities in e-mail, please take a look at A Quick Guide to E-Mail Security.) Microsoft allows you to turn off JavaScript in its e-mail programs; unfortunately, doing so will also disable JavaScript in Internet Explorer as well, where many Web pages rely on JavaScript to work. (This is what happens when a company intermingles program functionality for the sake of "convenience" and marketing instead of technical soundness.)
To disable JavaScript in Outlook, choose "Tools", and then "Options", and then select the "Security" tab. In the "Secure Content" area, choose the dropdown menu for "Zone" and select "Restricted Sites":
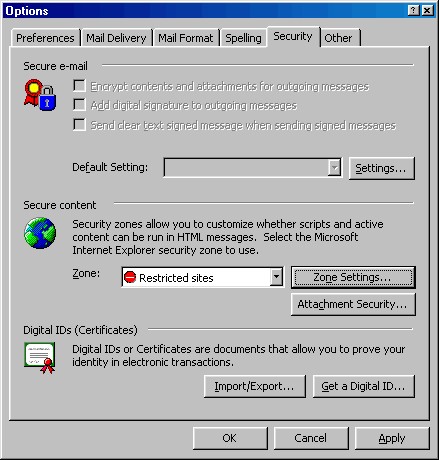
Fig. 4: Choose the Restricted Sites zone in Outlook
But wait, you're still not done! Now click the "Zone Settings ..."; button. A warning box will open informing you that you are about to change settings that will affect Outlook, Outlook Express, and Internet Explorer. Since we know that, click "OK". In the "Security" window that will open next, choose "Restricted Sites", as this image shows:

Fig. 5: Choose Restricted Sites on the Security tab of Internet Options control panel
Click the "Custom Level ..." button. Once the Security Settings window has opened, scroll down to "Active Scripting" and make sure that "Disable" is chosen. Click "OK" to close "Security Settings", click "OK" to close the Security window, click "OK" to close the Options window, and you're finally done.
If you use Outlook Express, the process is similar - after all, you're working with the same parts of the operating system that I described above for Outlook - but since this is Microsoft and everything has to have a different user interface, things are a bit different. Start by selecting the Tools menu, then "Options" and then select the "Security" tab. In the Security Zones section, select "Restricted Sites Zone (More secure)".
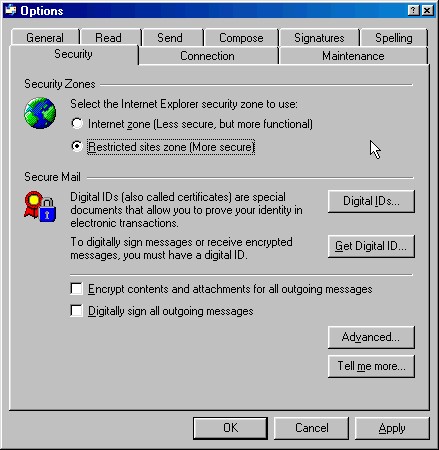
Fig. 6: Turn off JavaScript in Outlook Express
Now we need to set the Zone settings. Open "Control Panel" and choose "Internet Options". Click on the Security tab and choose "Restricted Sites", as this image shows (yes, this should look familiar to you - you just saw it above):

Fig. 7: Choose Restricted Sites on the Security tab of Internet Options control panel
Click the "Custom Level ..." button. Once the "Security Settings" window has opened, scroll down to "Active Scripting"and make sure that "Disable"is chosen. Click OK to close "Security Settings", click OK to close the "Internet Properties"control panel, and you're finally done.
Mozilla and Netscape 6 recognize the fact that many people prefer to enable JavaScript for Web browsing but disable it while reading e-mail. The preferences reflect this reality. In either the Web browser or the e-mail program, choose the Edit menu, then "Preferences", then "Advanced", and then "Scripts & Windows". At the top of the preferences page, you can set JavaScript as you best see fit.
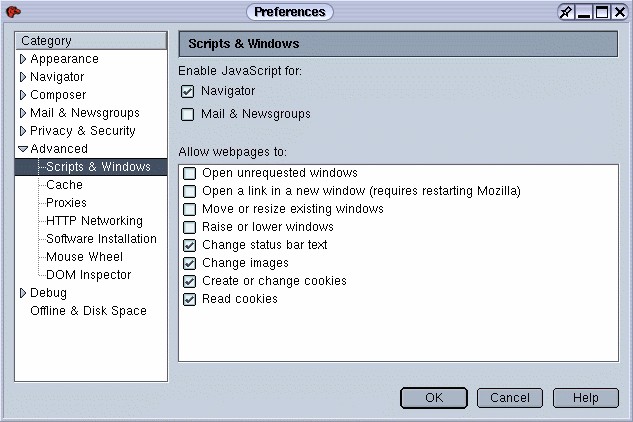
Fig. 8: Disable JavaScript for Mozilla/Netscape e-mail while leaving it on for Web browsing
Going Offline
The best way to stop Web bugs in their tracks is to read your e-mail while you're not connected to the Internet. After all, if a Web bug can't send information back to the mothership that spawned it, then it's useless. If you're connecting to the Internet via a dial-up modem, going offline is easy - just disconnect. If you're using broadband, like DSL or a cable modem, it's more complicated, but you can do it. However, do you really want to have to disconnect every time you read e-mail, and then reconnect when you're finished? If you're using a modem, the wait can be interminable.
Fortunately, there's a better solution. Several e-mail clients allow you to take the program offline without taking the entire computer offline. This allows you to read e-mail and reconnect immediately again as needed. You get the same effect as a disconnection, but it's far less hassle.
The fantastic Linux e-mail program Evolution makes this process especially easy. In the bottom left of the program's window is a small icon of two cables joined together. Simply click it, and Evolution is now reading your e-mail offline.

Fig. 9: Easily enable Evolution to work on- or offline
If you don't want the bother of clicking the little icon to work offline, Evolution can still accommodate you. Since Web bugs work, by and large, by using tiny, 1x1 pixel GIFs, if you could block those images, you'd be immune. Evolution has a setting that enables you to prevent images from loading off the Internet. This is something that none of the other e-mail clients I'm examining here offer. To use this feature, go to "Tools", select "Mail Settings...", go to the "Display" tab, and check next to the appropriate box, as shown below:
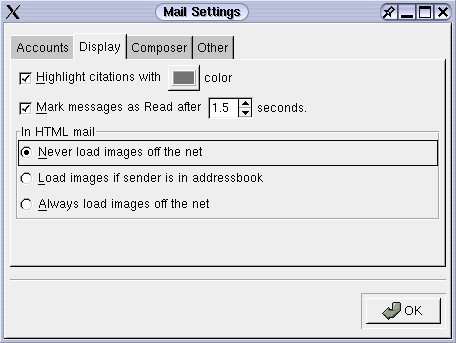
Fig. 10: Evolution allows you to specify what images you want to load in e-mail
Outlook and Outlook Express don't have Evolution's ability to block images selectively from the Internet in your e-mail, but they do make it easy to go offline. Simply go to the "File" menu and choose "Work Offline". Unfortunately, due to the way Microsoft tied its e-mail programs and Internet Explorer together, your choice to work offline in your e-mail program also prevents your Web browser from accessing the Internet. Since Linux doesn't tie programs together in the way Microsoft does, users of Evolution do not have that restriction. Of course, Windows users who use the Mozilla or Netscape browsers also don't have that limitation. It's possible to go offline in Outlook or Outlook Express and still use Netscape to access the Web.
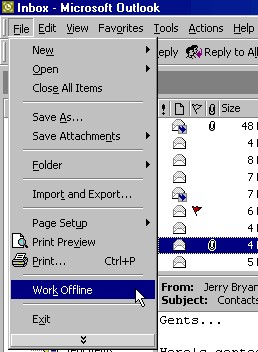
Fig. 11: Work offline in Outlook
You can also go offline easily if you use Mozilla or Netscape to read e-mail. In fact, you have two methods available. In the bottom right corner of the program is a little icon, similar to the one in Evolution, that enables users to go on- or offline with one click.
Fig. 12: Work offline in Mozilla/Netscape
Alternatively, you can choose the File menu, then select "Offline" and highlight "Work Offline":
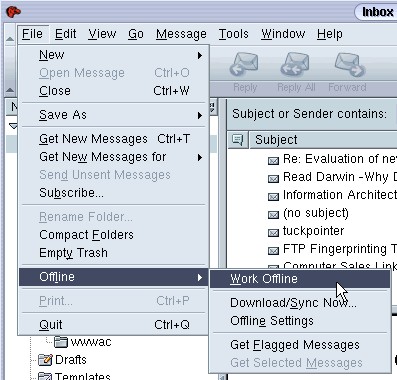
Fig. 13: Work offline in Mozilla/Netscape by choosing the Work Offline menu
One caveat: if you go offline in Mozilla or Netscape e-mail programs, the Web browser will also be taken offline. Since the e-mail program and browser are really aspects of the same program, this makes sense. But it can still be annoying if you find a Web address in an e-mail that you want to check out using your Web browser.
Encryption
Of course, the best way to protect the privacy of your e-mails as they travel over the wires of the Internet is to use encryption. If you encode your email messages, even if a spy got hold of them, he couldn't make sense of the gibberish he'd have in front of him. Only those who have the proper "key" to decrypt your e-mail messages will be able to read them. If you use strong enough encryption, you can feel well protected.
There are many programs you could use, but there are two that bear particular emphasis: PGP (Pretty Good Privacy) and GPG (GNU Privacy Guard), which is an open source replacement for PGP. Both are free and incredibly powerful. Both are not that difficult to use. And both support a wide variety of e-mail programs, including Outlook, Outlook Express, Netscape, Eudora, or Evolution.
A lot of ink has been spilled on the subject of encryption, so we're not going to recreate the wheel here. (The relevant links section at the bottom of this article includes a number of useful resources on PGP.) It's no longer particularly difficult to encrypt your e-mail. Just remember that the recipient of your message has to be able to decrypt it, so they need to have installed and configured an encryption program as well. The best way to learn how is to download PGP or GPG, create your public and private keys, and send yourself an encrypted test message. You'll be surprised how easy it really is, and you'll feel a lot safer.
Spam
I'm not going to spend a lot of time on the problem of spam. I loathe spam, and I'm not alone in my sense that it is increasing in quantity and obnoxiousness. The standard advice concerning spam - never reply to it, create good filters, and don't patronize companies that use spam - is sound, and I follow it myself. And there are certainly many Web sites that can help fight against the flood of junk mail we're finding in our inboxes; two such Web sites are spam.abuse.net and CAUCE: Coalition Against Unsolicited Commercial E-mail. Remember, spam is often a result of some sort of invasion of privacy, such as tracking which Web sites a user has been visiting, and too often it uses the tricks I've detailed above, such as Web bugs, to further threaten privacy.
Find Out Who's Selling Your Info
Even if you read and follow the advice given on anti-spam Web sites, you're probably still going to get bitten. You're going to get junk e-mail. But wouldn't it be nice to know who betrayed your information? Who sold your e-mail address?
Here's a tip that may help you. It won't work on every e-mail system, so you'll need to test it first. But when it does work, it's a powerful way to find out exactly what Web site sold you out.
Let's say a man's e-mail address is "bob.smith@widgets.com". Bob goes to The New York Times Web site and has to register in order to view the content. In the box that requests his e-mail address, Bob enters the following: "bob.smith+nyt@widgets.com". At the Slashdot Web site, Bob uses "bob.smith+slashdot@widgets.com". At Real Media's0 Web site, he puts in "bob.smith+real@widgets.com". And so on. Each time, he adds a plus sign, followed by a word describing the site, after his e-mail username and before the "@" sign.
A couple of weeks later, Bob finds some spam offering him a cheap cell phone. Bob groans ... more spam clogging up his inbox. But this time, Bob looks carefully at the header of the e-mail to see to whom it was sent. Aha! It wasn't sent to "bob.smith@widgets.com". Nope. Instead, it was sent to "bob.smith+real@widgets.com". Real Media sold him out!
As you can see, this technique can help you pinpoint exactly how a spammer got your e-mail address. At that point you can contact the company that sold your e-mail and change some marketing preferences that enabled it to sell your address, or you can choose to sever all ties with the company. The important thing is that people at the company cannot deny your accusation, as you have concrete proof.
There are two caveats about this trick. First, as I said above, it doesn't work for all e-mail systems. So send yourself a test message first. Bob, for instance, would send himself a message addressed to "bob.smith+test@widgets.com". If he gets the message, great. Things should work fine. If he never gets the message, maybe send one more, and if that one never arrives, assume that my technique just isn't going to work, at least as long as he uses the e-mail hosting company he's using.
The second caveat involves remembering what e-mail address you've used with all those sites at which you've registered. If Bob ever wants to log back in at The New York Times, he'll need to remember that the e-mail address he used is "bob.smith+nyt@widgets.com" and not "bob.smith+times@widgets.com". If Bob only registers at one or two sites, this won't be a problem. But if Bob is like most people and has registered at many sites, he'll need to either develop an ironclad system and stick to it, or keep a file on his computer that keeps track of the e-mail addresses he's used at various Web sites. It's not a huge deal, but it is something to think about. Many people find that the slight trouble of keeping such files is more than outweighed by the advantage of knowing exactly how their e-mail addresses are being used.
Conclusion
E-mail is important to all of us. It's convenient and powerful, and it helps us communicate in ways that were unimaginable just a few short years ago. However, we can't just assume that the e-mail programs we use will protect our privacy. Instead, spend some time and make sure that e-mail, that most powerful of tools, is working to benefit us in every way possible.
That concludes our brief examination of some of the privacy issues involved with e-mail. In the next, and final, installment of this series on privacy and the Internet, we will look at some privacy issues that are raised in other, more general use of the Internet.
Scott Granneman is a senior consultant for Bryan Consulting Inc. in St. Louis. He specializes in Internet Services and developing Web applications for corporate, educational, and institutional clients.
|